
Malware analysis

Analyze files privately and effectively
Cybercriminals are constantly developing more sophisticated malware and new attack methods to combat antimalware systems. Performing malware analysis, malware specialists. The Security Committee checks files and detects malicious activity, so it can quickly respond or eliminate threats before serious damage occurs.
- How can malware analysts contain and examine malicious code without executing it or affecting the system?
- How do the specialists for the Security professionals can quickly assess the latest threats and gain insights into cyber security best practices?
Enterprises need a comprehensive and vigilant malware analysis tool to combat next-generation attacks.
WHAT IS MALWARE ANALYSIS?
Malware analysis is the process of investigating the threat, intent and functionality of a given malware. This process will reveal the type, nature of malware and attack methodologies, etc., Which will enable incident response personnel, threat researchers and security analysts to quickly and effectively segregate and respond to security incidents, while finding the root cause of cyber attacks and improving their protection to protect their network infrastructure.
There are usually 3 types of malware analysis:
- Static analysis analyzes malicious programs without running them, mainly using signature-based detection and heuristic detection techniques.
- Dynamic analysis analyzes the behavior of malware when executed in an isolated environment that does not affect the actual system.
- Hybrid analysis combines static and dynamic analysis, providing malware analysts with the advantages of both approaches.
Business challenges of malware analysis
- False positive alerts due to use of one or more AV engines
- Concern for file privacy when uploading files to the cloud for analysis
- Time-consuming and cumbersome process due to the use of different sets of security products
- There is a shortage of specialists in the field. Internal cyber security, and the number of malware samples continues to grow
- No automatic analysis and corrective action
- Zero-day and advanced evasive malware bypassing limited malware analysis tools
Stages of malware analysis
Malware analysis can proceed in 4 different phases:
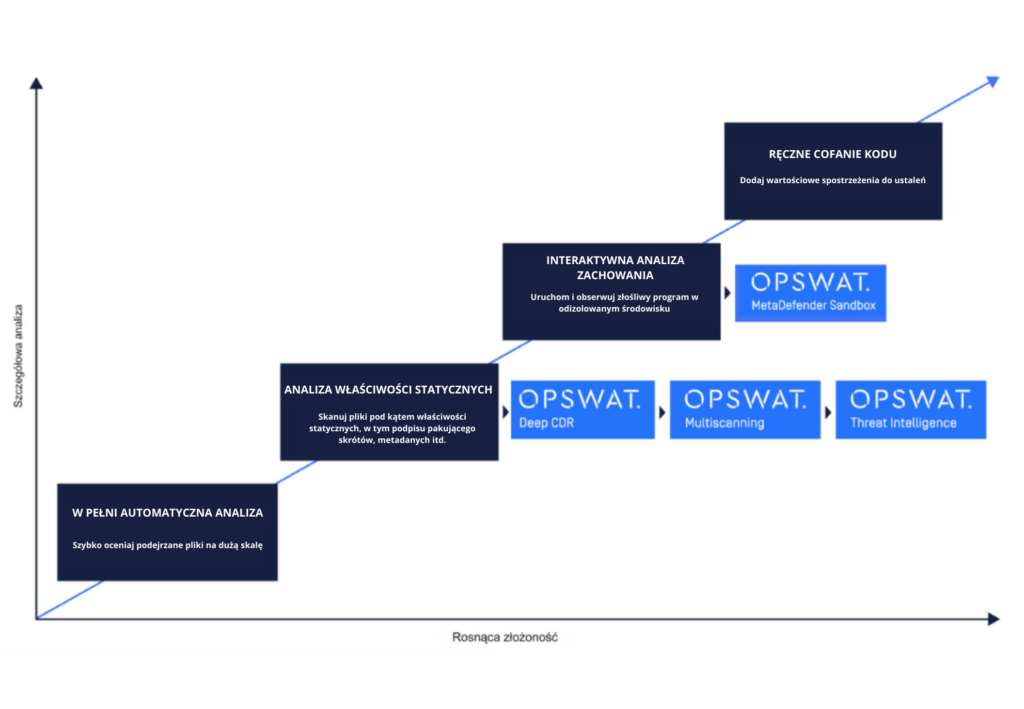

How can OPSWAT malware analysis help?
Keep your files private
You can control the privacy of your files, even locally or in the cloud. MetaDefender Core can be deployed locally, making it possible to analyze malicious files offline. Otherwise, using the MetaDefender Cloud platform, your files will be processed privately in temporary storage and deleted as soon as the analytics report is completed. This keeps confidential files private and keeps the scan results confidential, so criminals can’t use them for intelligence purposes.
Maximize malware detection rate
OPSWAT Multiscanning enables each file to be scanned with more than 30 malware protection engines, resulting in detection rates exceeding 99%. By combining detection methods based on signatures, heuristics, emulation, and machine learning, multiscanning helps stay ahead of new attack techniques. Our technology enables the system to process files at high speed and reduces false hit detection rates.
Run malware safely with behavioral analysis
The file’s suspicious behavior should be understood in its natural state. OPSWAT’s Sandbox technology provides enterprises with powerful dynamic analysis with error-avoidance techniques and flexible analysis configuration, bringing a detailed report on file behavior at execution time. In this way, the behavior of malicious content and executables can be monitored and understood, and enterprises can determine the best remediation path – before their systems are infected.
Take advantage of real-time threat analysis
Millions of malware attacks are carried out every day. Even known threats can get through traditional antivirus software. Our fastest file shortcut search service on the market – Threat Analysis quickly assesses a file’s reputation and investigates malware. It also provides analytical teams with the benefit of signatures provided by malware researchers from around the world, each of whom sees a different subset of malware samples.
Detect and prevent zero-day and evasive malware
Our best-in-class Deep Content Disarm and Reconstruction (Deep CDR) technology not only helps optimize incident response flow by delivering cleaned versions of files, but also supports malware analysis using forensic information. You can use Deep CDR to analyze suspicious objects embedded in files, such as macros, hyperlinks and OLE objects, without executing them. File extensions are examined so that seemingly complex files don’t look simpler and flagged as malicious content, alerting organizations when they are under attack.
Comprehensive automated analysis report
OPSWAT MetaDefender is more effective than any other competing malware analysis solution, leveraging both our industry-leading static and dynamic analysis technologies. Our fully automated tools generate comprehensive and detailed reports on the file under investigation, such as registry keys, file activity, process activity, network activity and more. All extracted data is automatically processed and reported via a real-time visual dashboard that enables the security team to block malware immediately. The process and policies can be configured to meet the unique requirements of the organization.






WHY CHOOSE OPSWAT MALWARE ANALYSIS
Enhance threat detection and prevention capabilities and minimize false alarms with OPSWAT’s best-in-class technologies that provide a more efficient and faster process for incident investigation and malware analysis.
Fast scanning and reconstruction of files in milliseconds without affecting performance. Scalability to any volume with built-in high performance architecture and load balancing features.
Fast and scalable implementation locally and in the cloud using REST APIs.
Administrators can create multiple workflows to handle different security policies.
A centralized user interface with a visual dashboard of real-time security status, providing full visibility of assets and immediate warning of potential threats.
We provide enterprises with powerful control over cyber security through a single platform that delivers higher ROI, higher adoption, lower overhead and fewer trained professionals needed to oversee complex systems.




