
FileScan

Prompt. In detail.
FileScan.IO is a Next-Gen Sandbox and free malware analysis service. It runs at 10 times the speed of traditional sandboxes with 90% less resource consumption, and its unique adaptive threat analysis technology also enables zero-day malware detection and more Indicator of Compromise (IOCs) extractions.
Constantly changing threats
We are in a technological arms race as threat actors are constantly refining their techniques and creating ever more sophisticated malware to evade security solutions.
This means that malware analysis systems must be able to effectively analyze these threats regardless of the evasive measures used and the level of sophistication.
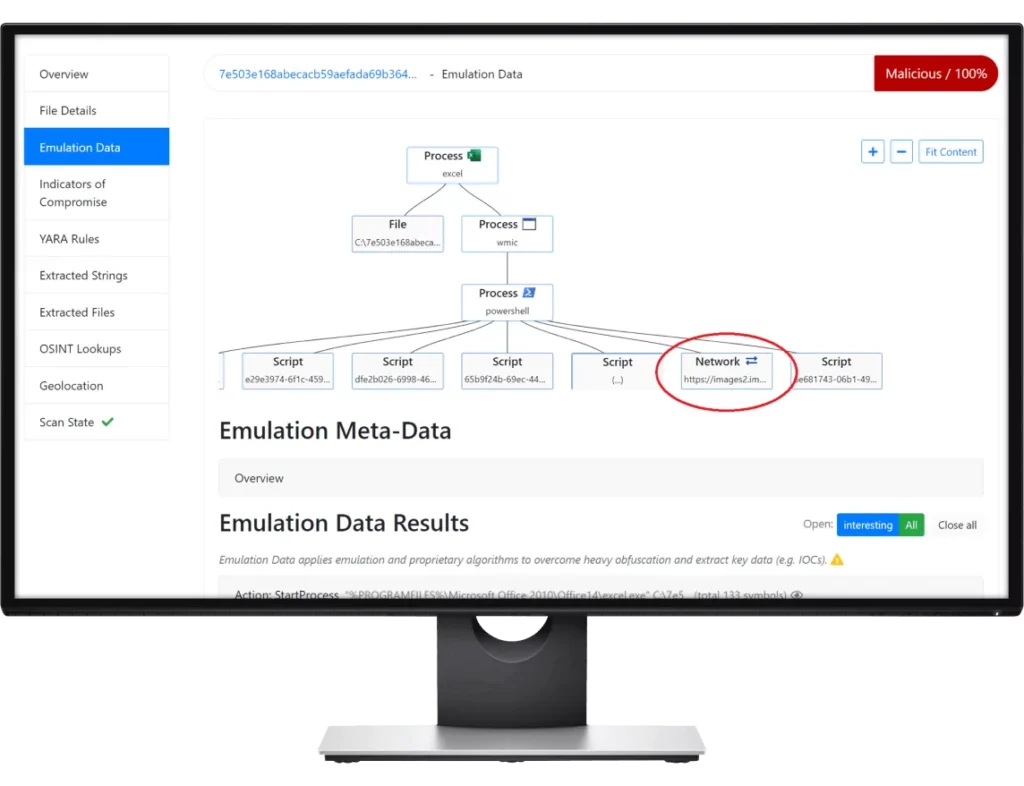
This analysis must be able to take the action of extracting built-in Indicators of Compromise (IOCs) for pre-emptive blocking measures, breach detection and proactive threat hunting in a post-breach scenario.
Strong obfuscation and encryption in malware means that only the actual execution of the malware (usually in an isolated environment, also known as dynamic analysis) was effective in extracting the necessary key IOCs (e.g., network IPs, URLs, domains) on a consistent basis.

FileScan – Next-Gen Approach
We asked ourselves a simple question: what if we could create a technology that would bridge the gap between static analysis and full-fledged VM-based sandbox systems?
We needed something that could scan thousands of files for malware in a short period of time, while overcoming layers of obfuscation to get to the “nuggets of gold” (IOCs) that are so invaluable – all with low resource requirements, easy maintenance and high efficiency.
Why OPSWAT FileScan?
- Perform IOC detection and extraction for all popular threats (files and URLs) in a single platform
- Quickly identify threats, their capabilities and update security systems
Search the corporate network for compromised endpoints - API-based framework for easy integration with existing systems
- Easy reporting for entry-level analysts and executive summary
- Easy deployment (in the cloud on platforms such as AWS or on-premises, including air gapped)
- Standard report export formats (HTML/PDF/MISP/STIX)

Adaptive hazard analysis
OPSWAT FileScan’s unique adaptive threat analysis technology enables zero-day malware detection and more Indicator of Compromise (IOCs) extractions.
Key features:
- Threat-agnostic file and URL analysis capable of massive amounts of processing thanks to a scalable architecture
- Focus on the extraction of intrusion indicators (IOCs), including the operating context for incident response
- Our patented Rapid Dynamic Analysis engine enables detection of targeted attacks bypassing anti-analytical tricks (e.g., geofencing)
Strong. Quick. Efficient.
Utilizing unique adaptive threat analysis technology, OPSWAT FileScan is built for power, speed and efficiency.
10x Faster – In any race, speed counts – and OPSWAT FileScan is ten times faster than a traditional sandbox.
100x More Efficient – OPSWAT FileScan is 100x more resource efficient than other Sandboxes.
Setup in less than an hour – In less than an hour, OPSWAT FileScan is up and running to help protect you from malware.
25,000 Files per Day – On a single server, OPSWAT FileScan can process 25,000 files per day.


FileScan – Competition comparison
The table below compares the current feature set of the OPSWAT FileScan engine with its peer group. This feature set does not include platform features such as API coverage, customizable ACLs, OAuth integration, CEF syslog feedback, etc. Please contact us to book a technical demo and explore all the features and capabilities of the platform.
| Function | FileScan.IO | Cloud online analysis tool A | Online cloud analysis tool B | Popular static analysis tools |
|---|---|---|---|---|
| Render URLs and detect phishing sites | yes | yes | No | No |
| Extract and decode almost all malicious VBA macros | Yes | No | yes | No |
| Analyze VBA stomp files designed for any system | yes | No | No | No |
| Shell code emulation (x86 32/64) | yes | No | yes | No |
| Export MISP (JSON) and STIX report formats | yes | No | No | No |
| Extract and analyze embedded PE files | yes | No | No | No |
| Decipher JavaScript / VBS | yes | No | Yes but limited | No |
| Decipher Powershell scripts | yes | No | Yes but limited | No |
| Analyze the structure of the METF Embed Equation exploit | yes | No | No | No |
| Analyze poorly worded RTF files | yes | No | No | No |
| Analyze Office binary file formats (BIFF5/BIFF8) | yes | No | No | No |
| Analyze the Strict OOXML file format | yes | No | No | No |
| Automatically decode Base64 strings | yes | No | No | No |
| Detailed annotated disassembly | yes | No | No | No |
| Decrypt password-protected office documents | yes | No | yes | No |
| Decompile Java | yes | No | yes | No |
| Decompile .NET | yes | No | yes | No |
| Calculate .NET platform GUIDs (module version/TypeLib identifier) | yes | yes | No | No |
| Classify imported APIs | yes | No | No | yes |
| MITER ATT&CK support | yes | No | yes | yes |
| Render PDF pages | yes | yes | yes | No |
| Extract embedded files (e.g. OLE2 from Word) | yes | yes | yes | No |
| Automatically tag samples based on signatures | yes | yes | yes | No |
| Support from YARA | yes | yes | yes | No |
| Generate text metrics (average word size, etc.) | yes | No | No | No |
| Detection of cryptographic constants | yes | No | No | No |
| Text analysis (guessed language) | yes | yes | No | No |
| Map UUIDs to known related files / metadata | yes | No | Yes but limited | No |
| Filter strings and detect interesting | yes | No | yes | yes |
| Extract and detect overlay | yes | No | No | yes |
| Integrated white list | yes | yes | yes | No |
| Detect alternative IOCs (email address bitcoin, etc.) | yes | No | yes | No |
| Calculate autentihash | yes | yes | yes | No |
| Verify Authenticode signatures | yes | yes | yes | yes |
| Analyze the RICH header | yes | yes | Yes but limited | yes |
| Calculate entropy of resources | yes | yes | No | yes |
| Detect domain URLs and IP addresses | yes | Yes but limited | yes | yes |
| Calculate resource shortcuts | yes | yes | No | yes |
| Calculate Imphash | yes | yes | yes | No |
| Calculate SSDEEP | yes | yes | yes | No |
| Extract PDB information | yes | yes | yes | yes |
| Detect TLS callbacks | yes | No | yes | yes |
| Solve known import ordinal numbers into names | yes | No | yes | yes |
| Anomaly detection (e.g., header checksum validation) | yes | Yes but limited | yes | yes |
| Query VirusTotal to check reputation | yes | yes | yes | yes |
| Packer detection (PEiD) | yes | yes | yes | yes |
| Detect file types | yes | yes | yes | yes |
| Calculate section abbreviations | yes | yes | yes | yes |
| Calculate the entropy of the cross sections | yes | yes | yes | yes |
| Extract strings from the executable file | yes | yes | yes | yes |
| Extract/hide resources | yes | yes | yes | yes |
| Extract/hide PKCS7 certificate | yes | yes | yes | yes |

Proven technology
Being very confident in the robustness of our technology and eager for feedback, we run a free community service at www.file-scan.io, which is verified by thousands of daily scans. This field test against fresh malware and phishing threats keeps our solution up to date, hardened and provides a high level of quality. As researchers at heart, we often try out cutting-edge technologies on the community platform, allowing us to quickly adapt to the latest cyber security trends. Only proven technologies make their way into an enterprise-grade commercial product.



