Don’t trust the files. Don’t trust the devices. Our Zero Trust Philosophy
Don't trust any file. Don't trust any device. Zero-Trust Philosophy.


Why OPSWAT?
Today’s businesses are plagued by cyber attacks. Threat actors are sending attacks through all available channels, and meanwhile the cost of protection is rising.
To address the challenges facing today’s enterprises and cut off the mainstream attacks, we offer two product platforms: MetaDefender for threat prevention and MetaAccess for cloud access control and endpoint compliance. Our guiding principles: don’t trust any file. Don’ t trust any device.

OPSWAT MetaDefender
Comprehensive cyber security platform for preventing and detecting advanced cyber security threats.
OPSWAT MetaAccess
Ensure that devices are security compliant before they can access any cloud applications or local resources, while providing enterprise-wide visibility on a single dashboard.



Why MetaDefender?
Companies are investing more resources than ever in cyber security – yet more and more breaches are occurring every year. Thousands of threat prevention solutions are available on the market, but most of them have one fundamental flaw: they are based on detection, but detection is never 100% perfect.
That’s why our advanced threat prevention platform, MetaDefender, is based on more than just detection.
MetaDefender uses unique deep disarming and OPSWAT (Deep CDR) content reconstruction to completely remove threats from files by reconstructing files, thereby removing potentially malicious active content and scripts. MetaDefender complements deep disarmament and content reconstruction with multiscanning, file-based vulnerability assessment and proactive data loss prevention (Proactive DLP).
Why MetaAccess?
The transition of enterprises to cloud computing, SaaS applications and bring your own device (BYOD) environments over the past decade has eliminated the traditional network perimeter, rendering most network access control (NAC) solutions obsolete.
To meet the challenges of today’s cloud-based environments and provide administrators with a cloud access control solution, we created MetaAccess. MetaAccess provides security for SaaS applications and data in the cloud. Enables access based on device status and compliance to help administrators block risky devices from connecting to sensitive cloud data and SaaS applications.


Solutions to help protect critical infrastructure
- Cross-domain solutions
- Secure access
- File transfer security
- Malware analysis
- Email security
- Network access control
Cross-domain solutions
Critical infrastructure must securely move data and devices between isolated network domains.
How do you secure file transfers across the enterprise, especially for devices you don’t control?
Transferring files into, across and out of secure environments is problematic. Files entering via mobile media and transient devices create opportunities for infection. Stored files can have zero-day attacks, temporarily unnoticeable and dormant on servers. Allowing files to leave secure environments risks leaking sensitive data. OPSWAT helps manage and secure the transfer of data or devices in segmented and airless network environments.
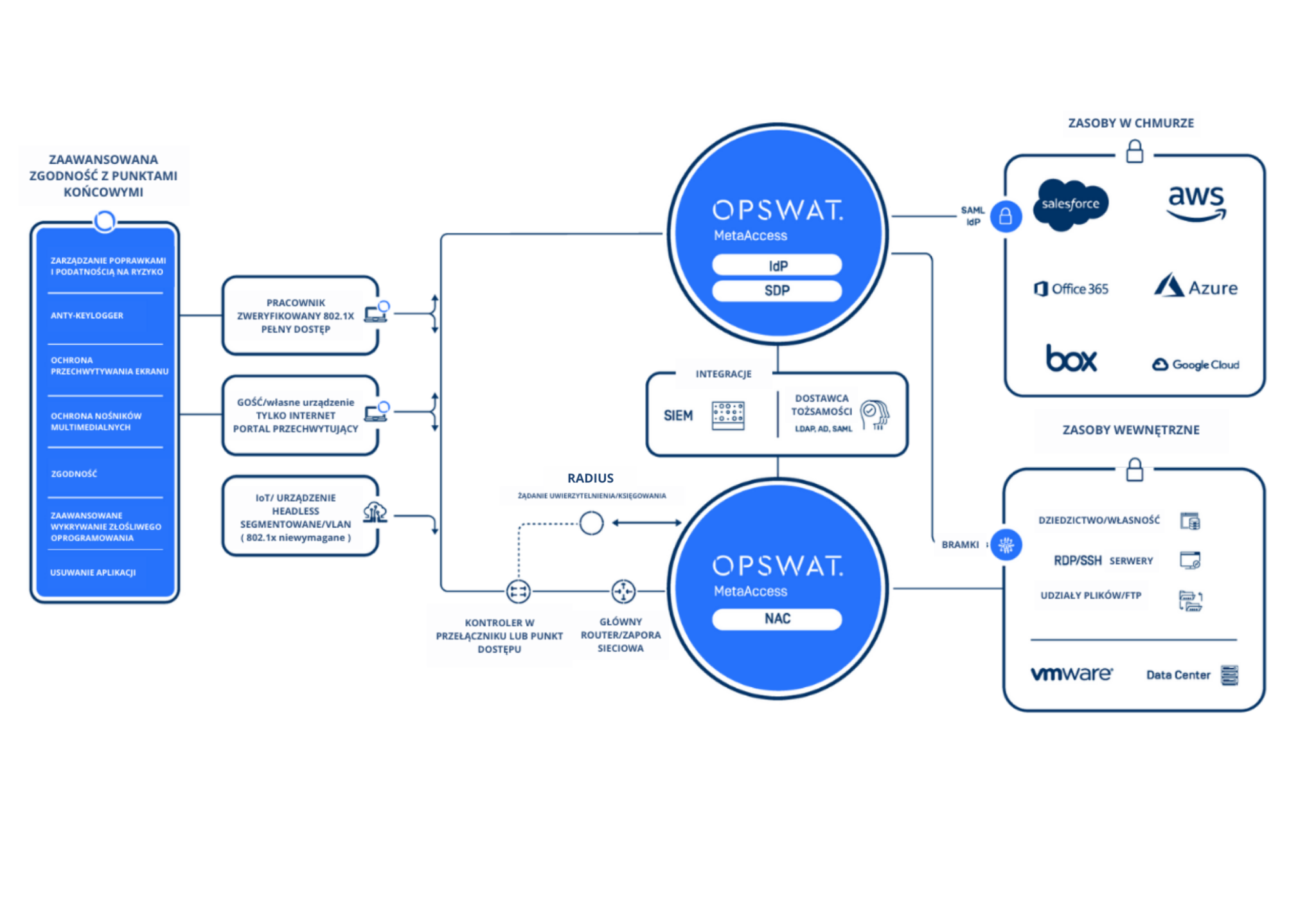
Secure access
Trust your endpoint to access the cloud and local networks
The proliferation of BYOD and cloud applications and the growing need for remote access to corporate data has accelerated the demand for secure access, including unmanaged device surveillance and compliance. It is more important than ever to go beyond basic tests, such as operating system level and antivirus protection, to include removable media, unwanted applications, keyloggers and screen capture protection. How can you verify that every device in your organization is security compliant before accessing an application or network, no matter where they connect from or where your data is located? At the same time, in addition to ensuring device security, organizations need secure access to networks, applications and data.
How can OPSWAT help?
The OPSWAT solution provides a single integrated platform to address each of these challenges and complexities. It is uniquely positioned to ensure that wherever your data is and wherever the user is, access and the device will be secure and compliant with your security policies. Implementing secure access for remote and local users and ensuring endpoint compliance for managed devices, BYOD and IoT can take months to a year, requiring senior engineers and network administrators, as well as outside consultants.
File transfer security
File transfer security solution
File transfer is essential to the effective operation of an organization and is needed for collaboration among the organization’s employees and to increase user productivity. They are a critical component of most Internet applications and services. However, they pose a serious security threat, as cybercriminals can compromise your servers or your entire system by sending malicious files. Traditional detection and prevention mechanisms are insufficient to prevent cybercriminals from trying to upload malicious content to penetrate your environment and steal your data. Integrating the many solutions needed to assess suspicious files and detect leaks of confidential data is costly and time-consuming. Enterprises need a robust layer of protection between the files they transfer and their network.
Why do you need protection?
Protect your users
- Do you allow user-generated or external content (resumes, invoices, forms, installers, patches, etc.) in your organization?
- Do you have a customer portal where you allow users to upload information / files?
- Do you provide any collaboration tools or file sharing services to partners and customers?
- Can you trust every file or installer downloaded or shared by your staff?
Attackers can target end users and infect their systems. They can steal sensitive information and personally identifiable information from them. Your collaboration and hosting platform may inadvertently host and distribute malicious samples that may contain illegal, offensive or copyrighted content/data, resulting in regulatory fines, costly lawsuits and bad publicity.
Protect your infrastructure
- Are you a large financial institution that accepts mortgage/loan applications, bank data, etc., or stores critical data such as credit card numbers, personal information of millions of customers?
- Are you a healthcare provider that receives and stores sensitive patient data?
- Can you trust every external file uploaded to web applications?
Hackers can bypass security and upload a new file or overwrite an existing file, which can be used to launch a server-side attack. They can then take control of your server and data, disable your site/app, use you for ransom, sell/disclose sensitive information, or upload more malicious files to your system.
Malware analysis
What is malware analysis?
Malware analysis is the process of investigating the threat, intent and functionality of a given malware. This process will reveal the type, nature of malware and attack methodologies, etc., Which will enable incident response personnel, threat researchers and security analysts to quickly and effectively segregate and respond to security incidents, while finding the root cause of cyber attacks and improving their defenses to protect their networks. infrastructure.
There are usually 3 types of malware analysis:
- Static analysis analyzes malicious programs without running them, mainly using signature-based detection and heuristic detection techniques.
- Dynamic analysis analyzes the behavior of malware when executed in an isolated environment that does not affect the actual system.
- Hybrid analysis combines static and dynamic analysis, providing malware analysts with the advantages of both approaches.
What do OPSWAT solutions offer?
- Keep your files private
- Maximize malware detection rate
- Run malware safely with behavioral analysis
- Take advantage of real-time threat analysis
- Detect and prevent zero-day and evasive malware
- Comprehensive automated analysis report

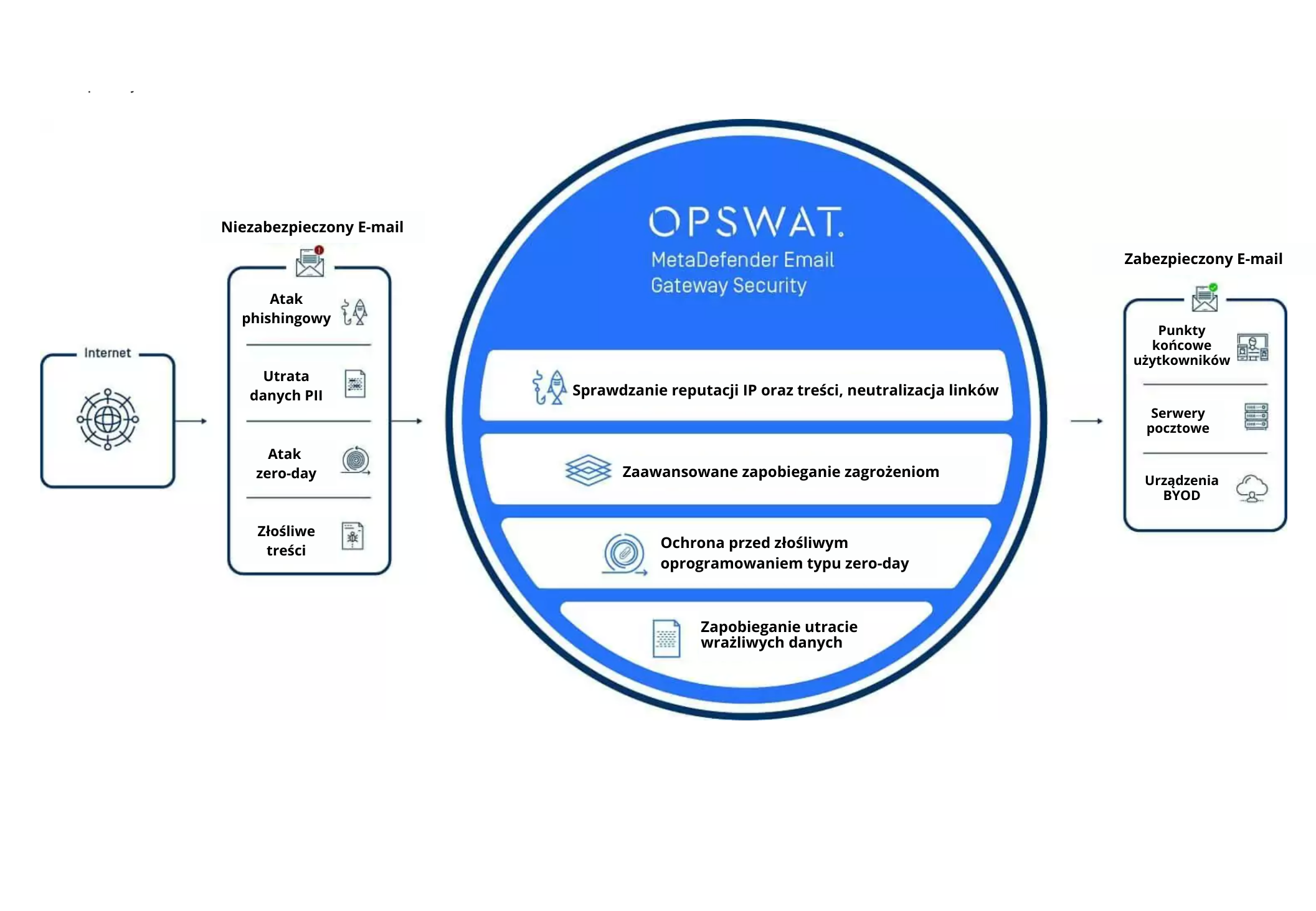
Email security
94% of malware attacks use email
The amount of malware is growing at a significant rate (it was 900 million new malware attacks in 2019), Which creates increased risks for any organization. 94% of malware is still initiated via email, costing companies more than $1.7 billion, according to FBI data.
Because these advanced threats can bypass many malware detection applications, OPSWAT follows a ZERO trust philosophy: trust no file, trust no device.
Protect your business with email security
OPSWAT provides four key benefits in the fight against email-borne threats:
- Protect users from spam and BEC attacks
- Use prevention-based technologies against targeted zero-day attacks
- Scan with the best malware protection solution, analyzing emails with 20 malware protection engines for the earliest protection against malware outbreaks
- Comply with industry regulations such as PCI, HIPAA, GLBA, RODO and FINRA by preventing emails from getting into or leaving your organization with confidential content
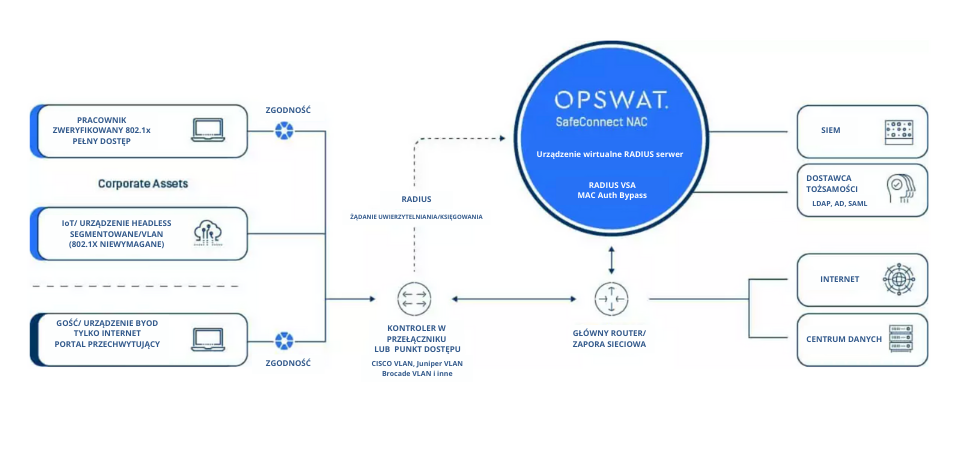
Network access control
Network Access Control (NAC) provides real-time network visibility and prevents risky BYOD, IOT and other devices from accessing network resources.
As the number and types of devices accessing the network grows, it is important to ensure visibility of all devices and their locations on the network. This prevents incompatible or risky devices from accessing the network or applications. NAC’s solutions enable full policy and equipment lifecycle management.
What happens if I don't implement the NAC solution?
Without NAC, it’s hard to be sure you know everything on your network, you can block unauthorized access, and all devices are safe. It is also much more difficult to demonstrate compliance with internal rules and external regulations.
Trust no file. Trust no device.
OPSWAT clients








OPSWAT technology partners





OPSWAT Platform as a tool to protect critical sectors
Check the application of all products offered under the MetaDefender and MetaAccess platform.
Challenges
Government organizations have become targets of attacks, and their vulnerabilities have been exploited by threats such as Stuxnet and Flame among others. led to the publication of confidential documents on WikiLeaks. Reports indicate that the number of cyberattacks on governments has increased significantly in recent years and is expected to be the most important threat to the United States and Europe in the near future. Government organizations must be able to protect themselves from unauthorized threats entering their systems, as well as from the loss of sensitive data.
Solutions
Metadefender OPSWAT solutions help government organizations secure their networks against external threats and data loss by enabling them to control the flow of data into and out of secure networks. Metadefender protects against the risk of malware getting in by allowing the configuration of detailed filters to inspect and “sterilize” digital data. Many organizations use Metadefender as a checkpoint for external secure media devices, such as USB drives, CDs, DVDs and memory cards, which undergo scanning. Organizations can prohibit external devices inside the network and connect kiosks to secure FTP so that scanned and approved files can be sent inside. Metadefender can also integrate data loss/leak prevention engines to check for files that an employee or contractor is about to take outside.
OPSWAT’s Metascan Metascan uses multiple anti-malware engine technology to scan content and is used by many organizations with concerns about file transfers between secure networks. By integrating Metascan into their existing transfer process, government organizations can scan each file with multiple antivirus engines to ensure they are “clean” before sending them to networks with higher risk status.
Challenges
Utility units and nuclear facilities are constantly vulnerable to cyberattacks and are grappling with the threat of malware infections such as Stuxnet. For this reason, government regulations have been implemented requiring these organizations to provide protection against cyber attacks.
Solution
In order to comply with new regulations that enforce protection against malware infiltrating an organization in several ways, many utilities have turned to OPSWAT’s solutions to ensure that threats don’t get in through USB drives, memory cards, or CDs/DVDs that employees and contractors bring with them. OPSWAT Metadefender provides control over the data entering inside a secure network, allowing you to configure multiple content filters based on file type, file size, anti-malware engine scan results and more. This allows utilities to create a secure mode of data flow and compliance.
Challenges
Organizations in the financial industry are responsible for a significant amount of confidential data, which they must protect from the growing number of cyberattacks targeting the industry. Financial institutions must comply with strict regulations that require them to adequately protect confidential data.
The law requires financial institutions to safeguard customers’ information and sensitive data. One of the requirements is to implement measures to prevent, detect and respond to cyberattacks, intrusions or other system emergencies.
Payment Card Industry Data Security Standard (PCI DSS) – PCI DSS requirements apply to all organizations that store, process or transmit cardholder data. One of the requirements that PCI imposes is the use and regular updates of antivirus software. The standards state that antivirus software must be used on all systems that may be attacked by malware to protect systems from current and emerging threats. In addition, the antivirus mechanisms must be up-to-date, active, and be able to generate logs for inspection. In addition, companies need to protect against advanced threats using non-standard malware that may not be detected by traditional antivirus software.
Securities and Exchange Commission – While current disclosure requirements do not specifically address cybersecurity, guidance from the Commission’s Division of Corporation Finance states that data security risk factors are an important consideration and that public companies should maintain security as part of their normal disclosure procedures. Implementing cybersecurity best practices to prevent data breaches will help limit a company’s exposure and liability in this area.
In addition to the obligation to protect customer data, organizations also face huge costs in the event of a data breach, which increases the importance of maintaining data security. To protect data and resist cyberattacks, organizations need to secure the network against threats from external sources, such as email, external media devices, users using remote access, and they need to make sure data is not leaked on lost or stolen devices.
Solution
OPSWAT’s solutions based on multi-malware-scanning engines help provide protection against known and unknown malware from a variety of sources. They reduce exposure to the occurrence of potential data breaches and help financial institutions meet security requirements.
Advanced malware protection:
Metascan provides advanced protection against malware that can target servers, workstations, Internet proxy servers, email servers and secure file transfer systems. Metascan offers multi-scanning with a maximum of 30 Anti-Malware engines. Using multiple Anti-Malware engines, the malware detection rate increases significantly and new threats can be detected faster. To protect against threats, including advanced zero-day and targeted attacks, Metascan offers data “sanitization” technology that removes possible built-in threats by converting files to a different format, such as converting to PDF format of a Word document and vice versa. Using multiple scanning engines and data “sanitization” technologies, secure networks can receive optimal protection against known and unknown threats. Metascan can help prevent cyber-attacks and ensure compliance with legal statutes, PCI DSS requirements, FSA, etc….
Email security:
“Spear phishing” is a popular cyberattack vector. Spear phishing emails will prompt the recipient to click on a link or open an attachment, which will install malware and provide access to the system. With Metascan Mail Agent or Policy Patrol Mail Security, all email attachments will be scanned by multiple Anti-Malware engines, and when using Policy Patrol Mail Security, any unknown embedded threats can be removed by changing the attachment file format. In addition, using file type verification technology, e-mail attachments attempting to spoof the file format can be blocked. By detecting and preventing spear phishing attempts, critical infrastructure systems can be protected from threats and unauthorized access. In addition, Policy Patrol Security for Exchange can perform content inspection and prevent the sending of emails containing, for example, credit card data, supporting PCI DSS compliance.
Security of portable media:
Portable media (such as USB drives, CDs/DVDs and mobile devices), provide another way for cyber criminals to gain access to a system. One known way was the Stuxnet worm, which spread via an infected USB drive. Widely used Metadefender ensures that all removable devices brought in by employees, contractors or suppliers are first scanned with multiple antivirus engines and are virus-free before they are allowed on a secure network. Metadefender can be installed on an endpoint or kiosk and can be used as a checkpoint to protect against portable media threats, preventing the possibility of data breaches.
Challenges
The energy sector, consisting of the oil, gas and chemical, electric and coal, and renewable energy industries, is constantly vulnerable to cyber attacks. High-profile attacks in the energy sector include “Energy Bear” (using the Havex trojan) and Icefog (using a backdoor called Javafog). The energy sector is particularly vulnerable because it holds valuable intellectual property and provides critical services that can be targeted by hacktivists or outsiders with sabotage and destabilization intentions. With existing systems built even decades ago that were not built with cyberattacks in mind, the power industry faces another challenge to invest in cyber security measures for systems. With the rise of increasingly sophisticated cyber attacks, the energy industry must keep up with the changing threat landscape. Cybersecurity regulations have been stepped up. The standards force energy facilities to achieve a high level of assurance that their critical systems are protected from cyber attacks by enforcing information flow controls, access controls for mobile and portable devices, and scanning devices for malware.
Solution
OPSWAT offers a multi-tiered approach so as to help energy companies protect themselves from cyber attacks and secure the various data flows into and out of the organization. OPSWAT solutions provide enhanced detection of known and unknown threats (including advanced threats). Email security measures and mobile media scanning, provide significant protection for critical infrastructure systems.
Advanced malware protection:
Metascan provides advanced protection against malware that can target servers, workstations, Internet proxy servers, email servers and secure file transfer systems. Metascan offers multi-scanning with a maximum of 30 Anti-Malware engines. Using multiple Anti-Malware engines, the malware detection rate increases significantly and new threats can be detected faster. To protect against threats, including advanced zero-day and targeted attacks, Metascan offers data “sanitization” technology that removes possible built-in threats by converting files to a different format, such as converting to PDF format of a Word document and vice versa. Using multiple scanning engines and data “sanitization” technologies, secure networks can receive optimal protection against known and unknown threats.
Email security:
“Spear phishing” is a popular cyberattack vector, including the Havex trojan and Shamoon virus which target the energy industry. Because spear phishing attacks target only a small number of people, they are harder to detect by a regular spam filter or a single antivirus engine. Spear phishing emails will prompt the recipient to click on a link or open an attachment, which will install malware and provide access to the system. With Metascan Mail Agent or Policy Patrol Mail Security, all email attachments will be scanned by multiple Anti-Malware engines, and when using Policy Patrol Mail Security, any unknown embedded threats can be removed by changing the attachment file format. In addition, using file type verification technology, e-mail attachments attempting to spoof the file format can be blocked. By detecting and preventing spear phishing attempts, critical infrastructure systems can be protected from threats and unauthorized access.
Security of portable media:
Portable media (such as USB drives, CDs/DVDs and mobile devices), provide another way for cyber criminals to gain access to a system. One known way was the Stuxnet worm, which spread via an infected USB drive. Widely used in the nuclear industry, Metadefender ensures that all removable devices brought in by employees, contractors or suppliers are first scanned with multiple antivirus engines and are virus-free before being allowed to operate on a secure network. Metadefender can be installed on a workstation or kiosk, and is commonly used as a checkpoint to protect infrastructure, SCADA-controlled environments, industrial control systems (ICS) and process control systems from the risk of infection by removable media.
Challenges
Several incidents in recent years, including false critical alerts triggered by McAfee and Microsoft Security Essentials, have highlighted the problems that resulted from misidentification of binaries detected as threats by any Anti-Malware engine (whether falsely or correctly): countless cases of customers losing time and resources to fix the problem. While software vendors cannot fully protect against such situations, proper precautions must be taken to be able to effectively detect malware.
Software developers also have to take on the challenge of making their applications compatible with other technologies. Incompatibilities can cause an unpleasant experience for users, degrade performance and even cause system failure. Anti-Malware vendors must evaluate devices for software incompatibility before installation. Security application providers need to make sure their products are compatible with the wide range of technologies and network solutions used to work remotely, so that customers can receive remote help and support and gain information about the status of their computer.
Solution
Metascan is ideal for software developers to scan binary files before release. By scanning with all the major antivirus engines, manufacturers can identify threats or false positives that must be removed before new software is released. Many manufacturers can also integrate Metascan into their solutions to add multi-scan functionality to their offerings.
AppRemover allows the Anti-Malware vendor to identify existing Anti-Malware software on the end-user’s computer before installation and provides the ability to uninstall it so as not to cause complications by running multiple Anti-Malware applications. This provides users with a seamless installation and reduces the number of problems reported to the manufacturer.
OPSWAT certification verifies the compatibility of workstation security applications with leading technologies and network solutions so that users experience fewer problems when they try to connect.
Challenges
With new malware emerging every day, identifying and analyzing threats is becoming an increasingly difficult task. Malware researchers working to enhance threat protection have a vast supply of samples of advanced malware to analyze, and investigative teams working to identify cyber criminals have a vast supply of unidentified files to wade through. These groups need a faster, more automated process for classifying known threats so they can focus their efforts on unknown files requiring analysis.
Solution
Metascan provides automated scanning solutions that can be integrated with “Malware researchers” processes to improve speed, efficiency and accuracy. By identifying known threats, Metascan reduces the volume of files that need to be sent for more intensive analysis, so customers can use their resources more efficiently. OPSWAT is also integrating its solutions with several technologies of the so-called “OPSWAT. “virtual test sandbox” (sandbox technology) to provide a complete, integrated solution for “malware researchers.”
Challenges
Companies in the healthcare industry and healthcare facilities must take extra precautions to ensure the privacy of confidential patient data is maintained, as required by the GIODO and HIPAA. The requirements are that organizations adequately protect the privacy of the protected electronic health information they collect, create, maintain or transmit. When these confidential data are breached (with increasing frequency), healthcare organizations are exposed to significant costs associated with the consequences of the breach.
Solution
OPSWAT’s technologies provide ideal solutions to each of these challenges faced by today’s educational institutions. AppRemover forces old security applications to be uninstalled so that new ones can be installed on all student and faculty computers. Metascan provides protection for email and file upload servers by scanning incoming files through a mechanism of multiple anti-virus engines, increasing confidence that malware will not enter the network. Many universities also use Metascan for their IT departments to facilitate malware research.
Universities that choose network solutions from vendors such as Juniper, Cisco or others to allow students and academics to access protected resources can specify a list of approved Anti-Malware applications by selecting applications certified by OPSWAT. These applications will be compatible with the university’s network solutions, and the OPSWAT video will also help explain to students why they should use the Anti-Malware applications on this list, so that fewer questions will be directed to the Help Desk.
Challenges
Companies in the healthcare industry and healthcare facilities must take extra precautions to ensure the privacy of confidential patient data is maintained, as required by the GIODO and HIPAA. The requirements are that organizations adequately protect the privacy of the protected electronic health information they collect, create, maintain or transmit. When these confidential data are breached (with increasing frequency), healthcare organizations are exposed to significant costs associated with the consequences of the breach.
Solution
Many breaches of confidential data could be prevented by ensuring that the right applications and security settings are in place on workstations. Correctly configured encryption software, for example, can protect sensitive data on a device, while monitoring the thousands of devices used by healthcare organizations is a daunting task for IT and network administrators. OPSWAT Gears allows organizations to remain GIODO and HIPAA compliant by enabling control over devices on the network. Gears allows administrators to monitor and alert on the status of end devices, including, for example, whether hard drive encryption software is installed and enabled.
OPSWAT solutions also help protect against malware that can compromise data security. Metadefender gives organizations control over the flow of data into and out of their secure network by enabling detailed data filters to be applied to different users and groups. Metascan provides multiple scanning engines integrated with existing security architecture to scan files in e-mail or file transfer servers. Metascan Client quickly scans for threats such as keyloggers on remote computers before they can access the network.
Challenges
While SSL VPN and NAC solution providers want to give their customers the ability to set access policies based on end-device ratings, the problem is the thousands of third-party applications that may be installed on these devices. Making sure all applications are compatible so that end users are able to pass a compatibility check is a challenge. Without building a team, they are not able to consistently provide support for new products, Vendors without a built team to provide support for their new products often rely on the potential of Microsoft Windows, which brings new problems, such as how to prevent forgery, how to perform needed remediation, what to do with Mac users and how to regulate solutions beyond Anti-Malware and firewall.
Solution
The OESIS Framework allows vendors to develop functions to reliably detect, classify and manage third-party applications across multiple categories on platforms: Windows, Mac and Linux installed on end devices. OESIS provides support for important corrective actions, as well as for types of applications not available through the WMI service. The OPSWAT team builds support for new features and applications so that your product/solution can keep up with the ever-growing list of applications, without having to engage an engineering team to do it.

Protecting you from the dangers of cyberspace.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.

OPSWAT, is a company located in San Francisco that provides IT infrastructure management and security software. Founded in 2002. OPSWAT provides solutions and technologies that protect devices and secure the flow of digital data. OPSWAT’s intuitive applications and comprehensive kits (development kits) are deployed by SMBs, large enterprises and OEM customers. They are currently used for more than 100 million workstations worldwide

We are a Polish IT company based in Warsaw, belonging to the “Value Added Reseller” (VAR) category. Our priority is to provide high-quality solutions and services based on products from reputable IT and telecommunications manufacturers. We distribute OPSWAT brand products providing our customers with assistance and support at every stage of implementation.
If you are interested in using our services, feel free to contact us by email or phone. You will find all the details in the footer below.

