
MetaDefender Core

MetaDefender Core
Advanced threat prevention solution
Cyber attacks are becoming more sophisticated. Cyber threats are constantly evolving and are being developed to evade traditional signature- and behavior-based malware defenses. Today’s IT and OT infrastructures require advanced, multi-layered threat protection to defeat zero-day attacks, advanced persistent threats (APTs) and advanced malware.
MetaDefender Core enables the integration of advanced malware prevention and detection capabilities into existing IT solutions and infrastructure to better handle common attack vectors: securing web portals against malicious file transfer attacks, expanding cyber security products and developing custom malware analysis systems.

Presentation of MetaDefender Core
Detect, analyze and eliminate malware and zero-day attacks
- Quickly scan all files with more than 30 top antivirus engines and detect more than 99% of known malware.
- Recursively clean more than 100 file types with market-leading Deep CDR technology and remove 100% of potential threats.
- Delete, edit or watermark sensitive data in files before they enter or leave your network.
- Detect vulnerabilities in installers, binaries or applications before installing them and plug any security holes.
- Monitor and secure all workloads in real time with central management and an interactive dashboard.
- Automated and actionable reports identify risks associated with users and services, enabling rapid corrective action.
- Configure workflow and analysis rules based on user, file source and file type to meet specific security requirements.

Features and benefits of MetaDefender Core
Prevent Zero-Day and Advanced Evasive Malware
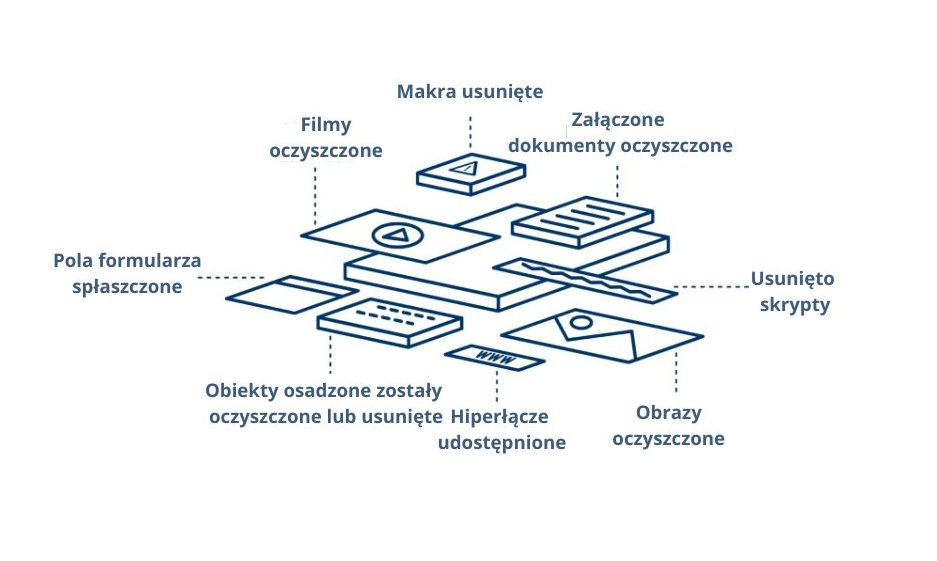
MetaDefender Deep Content Disarm and Reconstruction (Deep CDR) technology protects against known and unknown file-borne threats by cleaning and reconstructing files. Any possible risks embedded are neutralized while maintaining full usability with safe content. Reconstruct more than 100 popular file types, hundreds of file reconstruction options are available.
Achieve over 99% threat detection accuracy
MetaDefender Multiscanning technology uses more than 30 leading malware protection engines and proactively detects more than 99% of malware using signatures, heuristics and machine learning. This greatly improves detection of known threats and provides the earliest protection against malware outbreaks.


Prevent data breaches and regulatory violations
MetaDefender Proactive Data Loss Prevention (Proactive DLP) helps companies prevent confidential information in files from leaving or entering the company’s systems by checking their contents before they are transmitted. This helps companies comply with regulatory requirements such as HIPAA, PCI-DSS and RODO. MetaDefender Proactive DLP supports a wide range of file types, including Microsoft Office, PDF, CSV, HTML and image files.
Detect application and file security vulnerabilities
MetaDefender’s File-Based Vulnerability Assessment technology scans and analyzes binaries and installers to detect known application vulnerabilities before they run on end devices, including IoT devices. It gives IT administrators an opportunity:
- Check certain types of software for known security vulnerabilities before installation
- Scan systems for known security vulnerabilities when devices are at rest
- Quickly check running applications and the libraries loaded into them for security vulnerabilities


More than 100 file conversion options
Use the file type conversion function to flatten files into less complex formats. MetaDefend allows administrators to specify that certain file types are converted to other types (e.g., Microsoft Word documents to PDF). By adding this step to the processing workflow, zero-day attacks in which malicious objects are embedded in office documents or image files can be eliminated, even if they have the potential to evade detection by antivirus engines.
Verification of 4500+ file types
With MetaDefender’s file type verification technology, you can determine the actual file type based on the file content rather than an unreliable extension to combat fake file attacks. You can also configure security processes based on the actual file type. For example, you can take more precautions with risky file types such as EXE and DLL files – setting different rules or workflow rules based on the file type.
A forged file usually indicates malicious intent, so to reduce this risk, MetaDefender blocks files with invalid extensions. For example, MetaDefender can prevent EXE or DLL files trying to pretend to be TXT files from entering the organization.


Extraction of archives
MetaDefender currently supports archive scanning for more than 30 types of compressed files. Archive handling options are configurable, and encrypted archives are supported.
Benefits of archive extraction:
- Improve detection capabilities of malware protection engines using both extracted and non-extracted scanning
- Reduce scanning time and reduce processing time by removing unnecessary archive scanning
- Prevent archive bombing by extracting files and scanning them individually
WHY METADEFENDER CORE
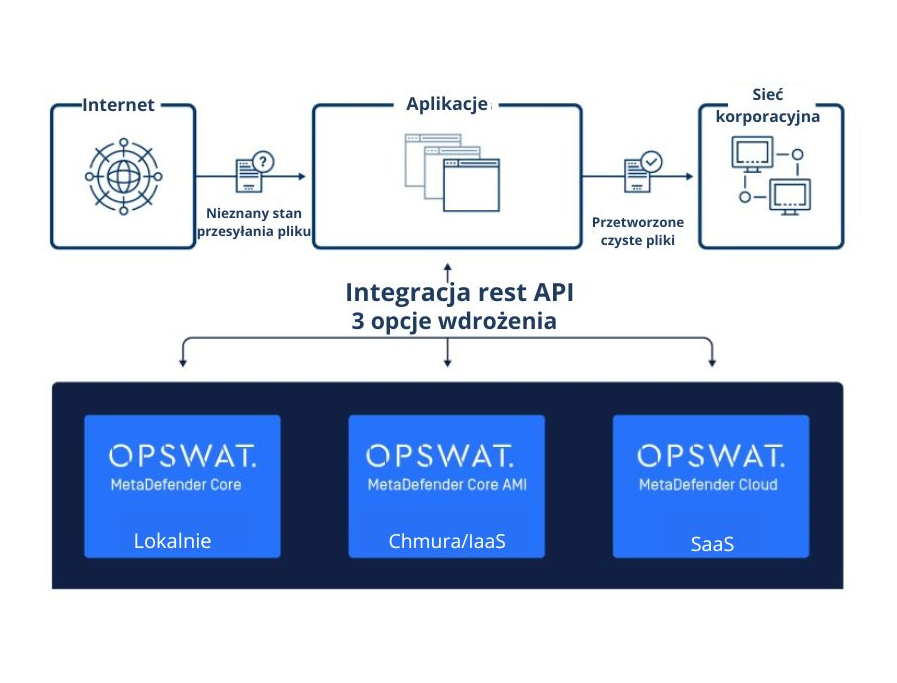
MetaDefender Core can be deployed locally, allowing offline file analysis. In the MetaDefender Cloud platform, your files will be processed privately in temporary storage and deleted as soon as the analysis report is completed.
Fast implementation both locally and in the cloud via REST API, Webhook or any product that supports ICAP (Internet Content Adaptation Protocol). Windows and Linux support.
Access to experts in the field. Cyber Security to tailor the solution to existing infrastructure and unique requirements. 24/7 technical support is available at all times.
From the centralized console, you can perform global operations, view all deployed malware protection engines, manage virus definitions and engine updates, and check license status.
Scale to any volume with our efficient architecture and load balancing feature. Fast scanning and reconstruction without affecting performance.
Single-source licensing through OPSWAT helps companies avoid the complex, costly and time-consuming implementation and management of different vendors.

Use Cases
Protect web portals from malicious file transfers
MetaDefender Core prevents the transmission of malicious files in web applications that bypass sandboxes and other detection-based security solutions. It also helps protect sensitive data, minimize data breaches and prevent privacy violations with Proactive DLP.

Perform malicious
software analysis safely and effectively
MetaDefender Core’s multi-layered malware detection and analysis technologies help quickly and effectively segregate and respond to security incidents, find the root cause of cyber attacks and improve security. It can be deployed locally, allowing malicious files to be analyzed offline to maintain the confidentiality of sensitive files and the confidentiality of scan results.
Extended threat protection for security products
Use MetaDefender Core to strengthen your security solution with OPSWAT’s advanced threat prevention technologies. We provide sample code and detailed API documentation to help you get your integration up and running. You can use almost any programming language to leverage MetaDefender’s technology with our APIs to help developers prototype quickly without an additional learning curve.






